Inspired by my diary entry “Malicious .iso Attachments“, @Evild3ad79 created a tool, isodump.py, to help with the analysis of ISO files.
Without any arguments or options, the tool displays its usage:

When you just provide it an ISO file, it does nothing:
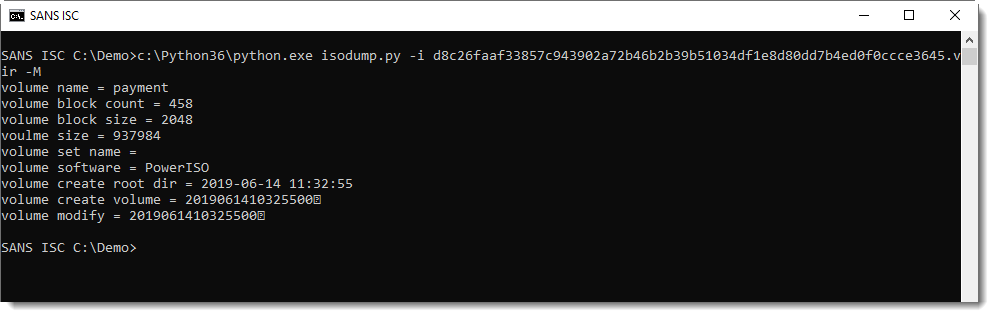
You have to provide a command, like displaying metadata (-M):
Or listing the content (-l):
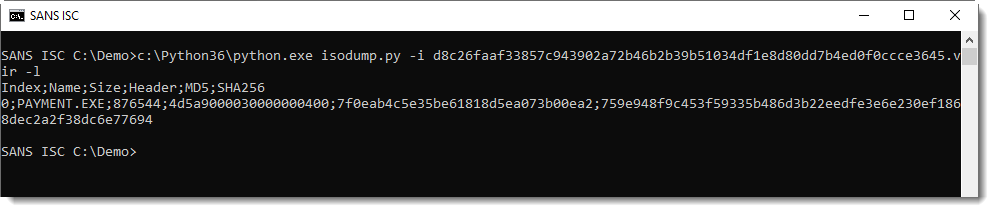
This ISO file contains a file named PAYMENT.EXE, it’s very likely a PE file (starts with 4D5A, or MZ). With the provided hashes, we can search for it on VirusTotal.
The file can be selected (-s 0) and dumped to stdout (-d). I like this feature, it allows me to pipe the malware into another analysis tool, without writing it to disk:
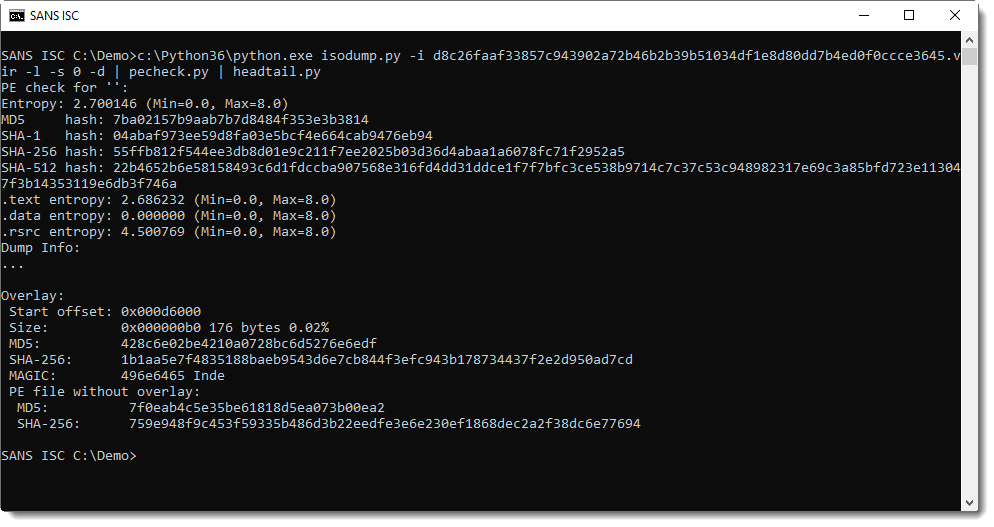
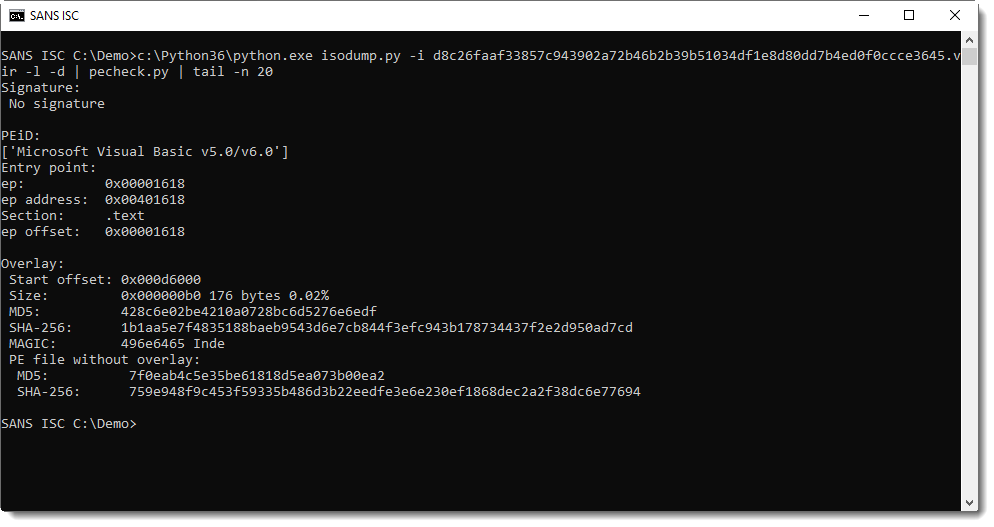
If you just need to look at the first file, you can omit option -s:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com
(c) SANS Internet Storm Center. https://isc.sans.edu Creative Commons Attribution-Noncommercial 3.0 United States License.